HOW TO BECOME A PENETRATION TESTER

If you're interested in computer security and have a talent for hacking and problem-solving, then a career as a penetration tester could be an ideal fit for you.
This role requires a combination of technical skills, analytical thinking, and creativity, making it a challenging and rewarding career option. In this guide, we'll explore the steps you can take to become a penetration tester, including the education, experience, and skills required to succeed in this field.
WHAT IS PENETRATION TESTING?

Penetration testing is a cyber security practice in which a skilled professional, known as a pen tester, attempts to simulate an attack on computer systems, networks, or applications to identify vulnerabilities and weaknesses in a system. The goal of a penetration test is to assess the security of a system and determine whether or not it is vulnerable to attack.
Corporations and government agencies rely on these specialized professionals to put their security to the test and measure its efficacy against malicious, unethical hackers. If, for instance, a penetration tester determines that a system is sound and incapable of being compromised by criminals or terrorists, the rest of the security team will assume that their job is done.
Penetration testing may be conducted as part of a regular security assessment after a system has been updated or upgraded, or as part of compliance requirements. A successful pen test can help organizations demonstrate their commitment to security and protect against potential security breaches.
WHAT DOES A PENETRATION TESTER DO?
A penetration tester has a lot of responsibility on his or her shoulders and their responsibilities only begin when they hack into a system. After that, they become part managers, part technical writers, and part security administrators.
They are the ones who perform simulated attacks on computer systems, networks, and applications to identify vulnerabilities and weaknesses. The goal of a penetration test is to identify security flaws before they can be exploited by malicious hackers.
Some specific tasks that a pen tester may perform include:
Identify Vulnerabilities in systems
The penetration tester will analyze computer systems, networks, and applications to identify potential vulnerabilities. This may involve using automated tools, such as vulnerability scanners, or manual testing techniques.

Exploit Vulnerabilities
Once vulnerabilities have been identified, the penetration tester will attempt to exploit them to gain unauthorized access or cause damage. This may involve using techniques such as social engineering, phishing, or network attacks.
Report test Findings
Not only will they need to assess the weaknesses in a network or certain devices, but they should be able to write reports that communicate these weaknesses. After the penetration test is complete, the tester will document their findings in a report. This report will typically include a summary of the vulnerabilities identified, their severity, and recommendations for remediation.
Strong written and oral communication skills are a necessary part of the profession. You will also need to have a good working knowledge of business and management to demonstrate the implications of the weaknesses you find.
For instance, you will need to be able to demonstrate any potential losses in terms of lost work hours, recovery time, loss of intellectual property, and other disruptions once you find a flawed system. If a sales team faces three days of downtime after a database is erased or corrupted, it will be important to show the financial impact that it could have on the company. Those findings will be presented to management with all appropriate visual aids to ensure that the case is clear to all stakeholders in the business.
Provide Recommendations
Penetration testers don't only assess problems but can be instrumental in formulating solutions to those problems. The pen tester may provide recommendations for improving the security of the system, network, or application.
This may include implementing new security controls, patching vulnerabilities, or improving security awareness training for employees. A good penetration test presentation will include suggestions for a network redesign or present a variety of software packages or coding approaches that can help secure the system from attack.
Retest (as necessary)
After remediation efforts have been completed, the pen tester may perform a follow-up test to ensure that the vulnerabilities have been addressed.
PENETRATION TESTER SALARY
According to the U.S. Bureau of Labor Statistics' most recent data, the average annual salary for penetration testers—or information security analysts—is $120,360.

ANNUAL MEDIAN SALARY OF
$120,360
Penetration Tester
With the wide range of knowledge and skills necessary to thrive in this job, it may be possible for a penetration tester to get an MBA and then move into a top position as an Information Security Officer or Information Systems Manager. The Information Systems Manager role position is known to pay above $100,000 per year, with a median yearly salary around $169,510.
HOW TO BECOME A PEN TESTER IN 5 STEPS
The job title penetration tester encompasses a wide range of skills and experiences. In order to succeed and thrive, a great penetration tester will have the coding skill to crack into any system. They should be very familiar with all aspects of computer security, from forensics to systems analysis.
It will also be of vital importance for them to have a full working knowledge of how computer security breaches can disrupt business and a full awareness of the financial and managerial implications of these breaches.
STEP 1: OBTAIN THE RIGHT EDUCATION
While a degree in cyber security or a related field isn't always necessary to become a penetration tester, it can provide a strong foundation in computer science, information technology, or a relevant field. It's important to have a good understanding of programming languages, computer networks, and cyber security principles.
STEP 2: LEARN PENETRATION TESTING
As a pen tester, you need to understand the inner workings of computer systems, networks, and security principles. You should be familiar with operating systems, networking protocols, programming languages, and databases. This knowledge is critical for identifying vulnerabilities and understanding how they can be exploited.
STEP 3: GET YOUR CERTIFICATIONS
Certifications such as Certified Ethical Hacker (CEH) or Offensive Security Certified Professional (OSCP) demonstrate your proficiency in ethical hacking techniques. They can help you stand out to potential employers and give you a competitive edge. These certifications also show that you understand the importance of ethical hacking and have the skills to perform penetration testing ethically.
STEP 4: GAIN PRACTICAL EXPERIENCE
Practical experience is essential to becoming a successful pen tester. Consider participating in bug bounty programs, working on projects, or volunteering for cyber security-related initiatives. This experience helps you understand real-world scenarios and learn new techniques for identifying vulnerabilities.
STEP 5: DON'T STOP LEARNING!
Cyber security penetration testers need constantly update their skills, knowledge, and methods for hacking systems. They need to study new security software packages and learn all they can about new protocols in security teams so that they can find vulnerabilities. A good penetration tester is always learning to stay up to date with current technologies and how they can be exploited.
As technology continues to evolve, you need to stay up to date with the latest tools and techniques. Continual learning is essential to remain relevant in the industry. Attend conferences, participate in online communities, and keep up with cyber security blogs and publications to stay up to date with the latest trends and best practices.
VISUALIZATION OF STEPS TO BECOMING A PEN TESTER
The following graphic should give you an idea of what is involved if you decide to aim your career path toward the penetration testing profession.
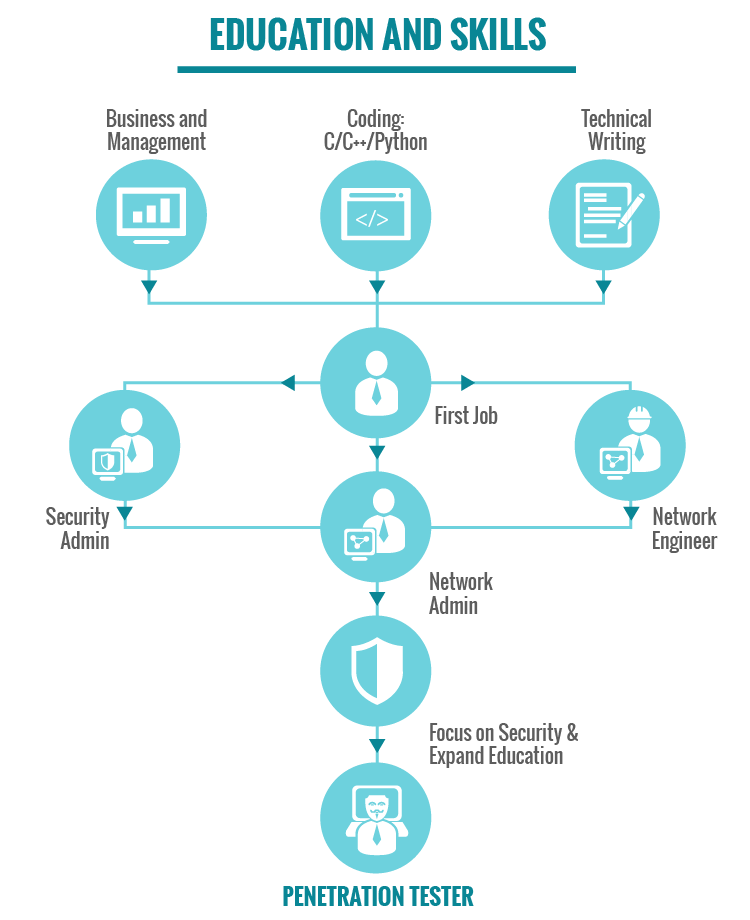
POSSIBLE PENETRATION TESTER CAREER PATHS
The path to penetration tester is not quite linear as there are many ways to approach this interdisciplinary field. Thus, there are several possible career paths for a penetration tester, some of which are:
Pen Tester
Working as a full-time penetration tester for a company, agency or consultancy firm, where the primary job responsibility is to conduct security assessments of systems, networks, applications, and infrastructure.
Security Consultant
Providing consultation and guidance to organizations on how to improve their security posture by identifying vulnerabilities, recommending solutions, and developing security policies and procedures.
Ethical Hacker
Performing ethical hacking and testing activities to identify and report vulnerabilities in systems, networks, applications, and infrastructure. They may work for a company, agency or consultancy firm, or as a freelancer.
CYBER Security Analyst
Monitoring, analyzing, and investigating cyber security incidents and breaches to identify the root cause, assess the impact, and recommend remedial actions. A cyber analyst is a very common career starting point.
Security Architect
Security architects are in charge of designing, implementing and maintaining security systems, networks, and applications to protect against cyber attacks while ensuring compliance with relevant regulations and standards. A security software developer role is another common path in this step of the career ladder.
Cyber security Manager
Managing the overall cyber security program of an organization, including risk assessment, policy development, incident response planning, and security awareness training.
Forensic Analyst
Conducting forensic analysis of digital evidence in cases of cybercrime or other criminal activity, to identify and reconstruct the events leading to the incident.
Researcher
Conducting research and development in the field of cyber security to advance the state of the art, develop new tools and techniques, and improve the effectiveness of security systems and processes.
JOBS SIMILAR TO PEN TESTING
Not many jobs entail quite the scope of a penetration tester, but the career does touch on so many that there are a lot of related specialties for a tester to branch into or from. Computer and Information Research Scientists study and solve complex problems for businesses, medicine and science, while computer systems analysts help organizations operate more efficiently and safely. Network and computer systems administrators are responsible for the day-to-day security and operation of computer networks in businesses and almost every type of federal and state agency.
PENETRATION TESTER VS. SECURITY ADMINISTRATOR
The two may seem like adversaries, but they're both working to strengthen the same system.
- The security administrator is charged with designing and implementing security systems and protocols for his or her department or company.
- A penetration tester on the other hand, will try to find ways to undo the security administrator's work. They will spend time researching how to hack into the administrator's systems and then will write reports to show the vulnerabilities and their business implications.
When a penetration tester and security administrator work together and strive to find the very best solutions for their network, then the company or department benefits.
Though their work frequently seems to be at odds, the duties of a penetration tester and a security administrator frequently overlap, and each tends to inform the other. They need to be able to assess the best security technologies within budget parameters and then assure that their team is capable of rolling out those products in a timely and effective manner.
TAKE THE FIRST STEP TOWARD your new career
Becoming a penetration tester requires a strong foundation in IT, practical experience and a commitment to ongoing learning. Obtaining professional information security certifications and degrees can help demonstrate your expertise and stand out to potential employers. Understanding the importance of ethical hacking is also critical to becoming a successful penetration tester.
To find a school and get started on meeting the educational requirements of becoming a pen tester, use the Find Schools widget on this page and get matched with a school. You'll find that there are plenty of online cyber security degree options to choose from as well if you are short on time and/or cannot attend school in person.
